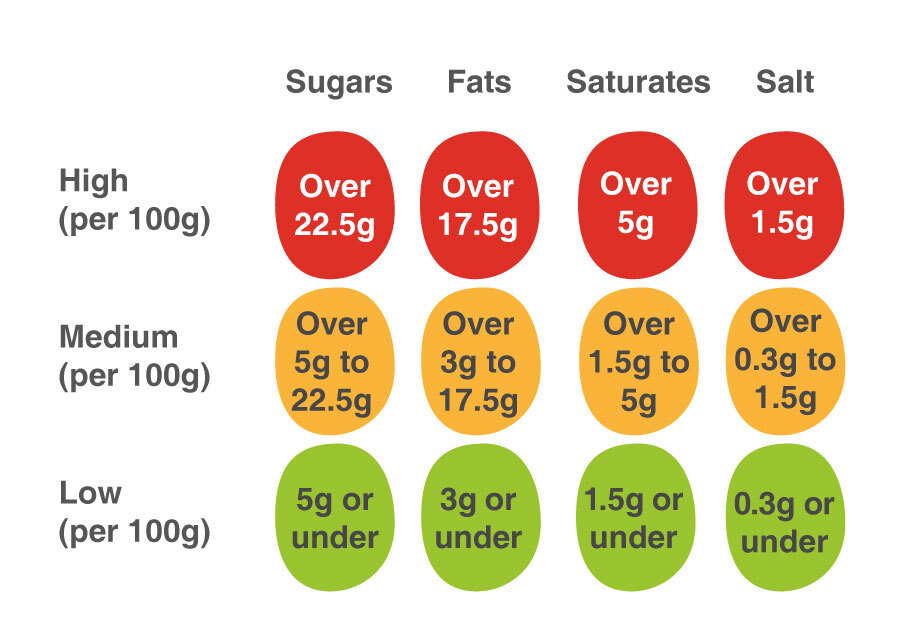
Indeed there is some evidence that consumers find traffic light labeling useful in determining their food choices. Unfortunately there's currently no good way of aggregating all of the food choices you make together to demonstrate what you're eating like on a daily or weekly basis. Can you have that cheeky pizza or tub of ice cream without going over your calorific recommendations? How many greens equal a red?
There's a whole bunch of calorie tracking applications out there but they can be fiddly and I find that of the one's I've tried generally I end up manually inputting information about what I'm eating, this is time consuming and a real pain in the ass. This is because these apps need to know what products you're eating. They maintain a database somewhere that looks up EAN codes and hopefully returns you some useful information. This is where many apps in the UK fall down with only limited coverage of our millions of food and drink options.
I think the standardization of a traffic light style system is useful but unless you're very strict when shopping, it's difficult to know what ratio of green, amber and red makes sense.
Instead I suggest that supermarkets work to make the nutritional information about a product available in-store in a computer-readable way. Two obvious ways to do this are NFC and QR codes. The smartphone is ubiquitous and if nutritional information were trivially accessible it would be trivial to write apps that can accurately track your purchases. Applications could easily be created that look at this data over time, or look at whole-family purchases to busy parents make more informed decisions and understand better what their consumption patterns are really like.
I mention NFC and QR codes above, these could deployed in two ways - on products or on the shelf, this is a very cheap option as supermarkets are constantly changing and updating their labeling anyway. On products would be more expensive but has the advantage that users could scan their items at home, as they're consumed as well as the time of purchase.
Another benefit of presenting this information in a tech readable way is that it's easy to add a bunch more information than just traffic lights. You can add information on how many vitamins are provided in this product and allergy information too.
Tills could read this information so even if you didn't walk around with a smartphone at all the till could print out the nutritional information about your weeks shop on your receipt, even pointing out things that are on offer which would supplement your diet, of course they could do this when they look up the EAN codes but this requires lots of work, chatting with a product database etc the nice thing about presenting the information locally i.e on the products is that the calculating of nutritional information and ratios becomes simple.
Imagine walking around a supermarket, you've told the application on your phone that you're doing a weeks worth of shopping. The application knows that you're trying to loose weight, that you need a certain amount of protein in your diet and that you're allergic to nuts. As you walk around the supermarket each item is scanned as you put it in your basket. You get a little beep to let you know that the fancy bread you just put in may contain nuts and you get a readout telling you if your diet this week is going to be higher in fat than you'd like or if you need to go grab some chicken because it's low in protein. A good application would probably store your previous purchases in a database so that that it can show you trends over time. If products did have a QR code printed next to the traffic light label then it would mean that once you've done your shopping and returned home you could track what you're eating, as you eat it. That would allow you to do some really interesting analysis of your eating habits.
There's lots of scope here for a supermarket to create an app that does all this and in turn offers targetted adds, perhaps specific discounts etc - there's a lot that can be done.
I like the idea of having the information in the QR code because it means I don't need internet access on my phone and makes the technological requirements for understanding the nutritional value of an item very low. Camera + QR reader = Done. When you make something like this Cloud based you have to be able to connect (WiFi or 3G) download (IP/TCP Stack) and interpret data from the supplier. However, something that used the QR code to grab a link to some Cloud based resource would perhaps be more valuable to a supplier. Who would be interested to know that their items were getting scanned 100k times but only being purchased 10% of the time? - they need to look at their nutritional info. I think this is exciting as it would allow users to start driving nutritional requirements back up to suppliers in a very real way, rather than focus groups and surveys.
For me, I'd like nutritional information on packaging exposed in a way that my phone can interpret, then I can spend weeks writing an app to help me with my dieting rather than going for a run!